Phishing Website Investigation with Whois XML API and Threat Intelligence Platform Toolsets
Arguably, the most ironic phishing incident to hit American corporations occurred shortly after the infamous Equifax data breach. In September 2017, hackers broke into the networks of the credit reporting bureau Equifax and stole the private details of about 60% of the population of the United States; that is, every American of working age. They made off with the names, addresses, drivers' license numbers, and social security numbers of 143 million consumers.
Only days later, Equifax launched the website equifaxsecurity2017.com to answer the questions the consumers had about the hacked account and to apply an account protection service. Unfortunately, Equifax staff actually linked the official Equifax Twitter account to a fake site, securityequifax2017.com. A software engineer named Nick Sweeting created the fake website to make a point to Equifax -- and, as one would expect, the entire corporate world -- how they set themselves up to be defrauded.
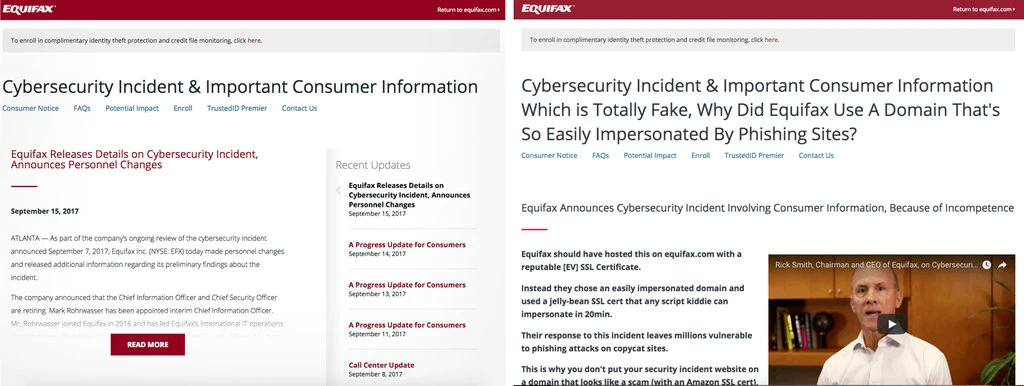
The fake Equifax website (Source: New York Times)
The estimated 200,000 people who logged onto the account on the fake website saw a message that read, “Cybersecurity incident & Important Consumer Information Which Is Totally Fake, Why Did Equifax Use A Domain That’s So Easily Impersonated By Phishing Sites?” The identity theft protection website required the surname and the last six digits of their Social Security numbers to enroll on the Equifax program. Mr. Sweeting’s website did not keep the information. He took the site down within a few days of posting it.
“It only took me 20 minutes to build my clone. I can guarantee there are real malicious phishing versions already out there.” Because phishing websites are so easy and inexpensive to build, the internet is awash with online portals that fool end-users into believing they represent real brands.
Every day, information security forensics researchers uncover the origins of phishing websites through the use of cybersecurity tools such as those that WHOISXMLAPI.com and ThreatIntelligencePlatform.com provide.
WHOISXMLAPI.com and ThreatIntelligencePlatform.com Phishing Domain Research Tools
The researchers at WHOISXMLAPI.com and ThreatIntelligencePlatform.com came across a phishing website for Xfinity (a division of Comcast). Xfinity supports television and internet services. At the end of August 2019, he website appeared on several blacklists. We chose to apply WHOISXMLAPI.com and ThreatIntelligencePlatform.com forensics toolkits to see if we could reveal who was behind the fraudulent website.
WHOISXMLAPI.com offers information security forensics professionals the Dashboard Domain Research Suite, and ThreatIntelligencePlatform.com provides the Domain Name Analysis to get to the bottom of phishing websites.
Both kits provide users with the ability to look behind the facade of websites to discover their origins. In some instances, the tools can excavate the physical location in which hackers created the website. The location can sometimes provide circumstantial evidence with regard to the authors of the phishing site, as well.
WHOISXMLAPI Domain Research Suite
WHOISXMLAPI Domain Research Suite provides a means of revealing the domain’s current and historic information of behind a website. Users can search by domain name, contact and registrar addresses, country, and more. The tools we used in the Suite include:
- WHOIS Search
- WHOIS History Search
- Reverse WHOIS Search
The ThreatIntelligencePlatform.com Domain Name Analysis can resolve the IP addresses of domains, and reveals the domain infrastructure information. It delivers a lengthy, highly readable report based upon results from a single input. Some of the infrastructure information includes geolocation data attached to an IP address, the domains related to an IP address, the status of the SSL certificate for the IP, whether the domain has been blacklisted on malware lists, and more.
ThreatIntelligencePlatform.com Domain Name Analysis
The research team used the GUI tools to reveal at a domain level how the website was fake, and, if possible, the probable origin of the phishing portal.
An Investigation into a Real Fake Website
Hackers make their business by creating phishing versions of well-known brands. The brands have a built-in level of authority and credibility as consumers give them a great deal of trust. The most popularly phished websites are in the financial sector, since “that’s where the money is.” E-commerce sites are also popular since users share critical personal contact details with sellers and make funds transfers to sellers.
The website our research team found appeared on several blacklists as https://x-finitycomcastboxappsuitnewteam.duckdns.org/xfinity. Xfinity is one of the largest cable providers in the United States. The interface most likely displays after a user clicks on a link in an email that tells them that they have a billing issue, probably a late billing problem.
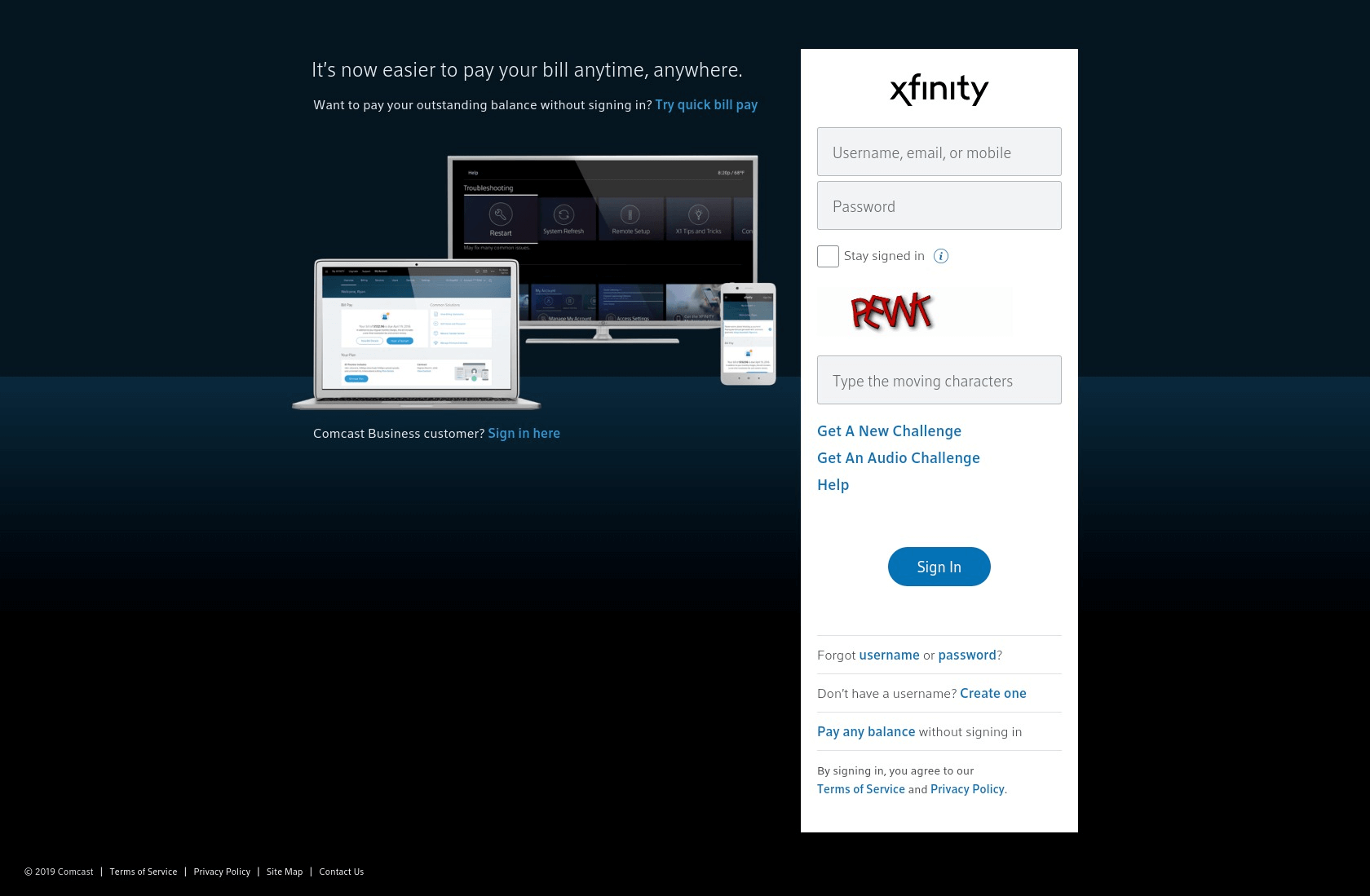
A fraudulent Xfinity website
The website makes it as easy as possible for the unsuspecting user to enter critical private information. Its simplicity belies its malevolence. However, the sheer length of the domain address informs us of an entity not associated with Xfinity created the domain. One dead giveaway that the domain name is not trustworthy is the reference to “x-finity” instead of “xfinity”. And then, of course, there is the .org designation. Xfinity as a commercial corporation does not use the non-profit .org top-level domain designation. The duckdns reference implies the IP address is a dynamic one.

DuckDNS.org home page
Domain administrators use dynamic DNS servers for a continuous mapping of changing IP addresses to a domain name. Dynamic DNS servers help users on the internet to always find a domain by its domain name, even though the IP address of the device that hosts the domain changes. Usually, residential and small business users elect to use DNS Dynamic addresses. Most enterprises specifically require static addresses. Thus, another clue about the nature of the domain is that whoever launched it did it from a home- or small organization-based location. It is definitely not associated with the Xfinity group of related subdomains. Researchers posit that it was a home-based effort.
Dynamic IP addresses pose a problem if the customer wants to provide a service to other users on the Internet, such as a web service. As the IP address can be changed frequently, corresponding domain names must be quickly re-mapped in the DNS, to maintain accessibility using a well-known URL. A quick look at its root domain address, https://x-finitycomcastboxappsuitnewteam.duckdns.org/, reveals a basic file directory, instead of the x-finity.com homepage.

Screenshot of https://x-finitycomcastboxappsuitnewteam.duckdns.org
WHOIS Behind the Fake Website?
A look at the WHOIS record in the WHOISXMLAPI Domain Research Suite of GUI tools illustrates that the only information to be found about the registrant is a name -- Gandi SAS -- and Registrant State/Province: Paris and Registrant Country: FRANCE. Of course, Paris is neither a state nor a province. In addition, the record lacks contact details like the address, phone numbers, and email addresses. However, a quick search on Google does indicate Gandi SAS is a French domain registrar company. Apparently, the registrar requires very little in confirmation of ownership of domains.
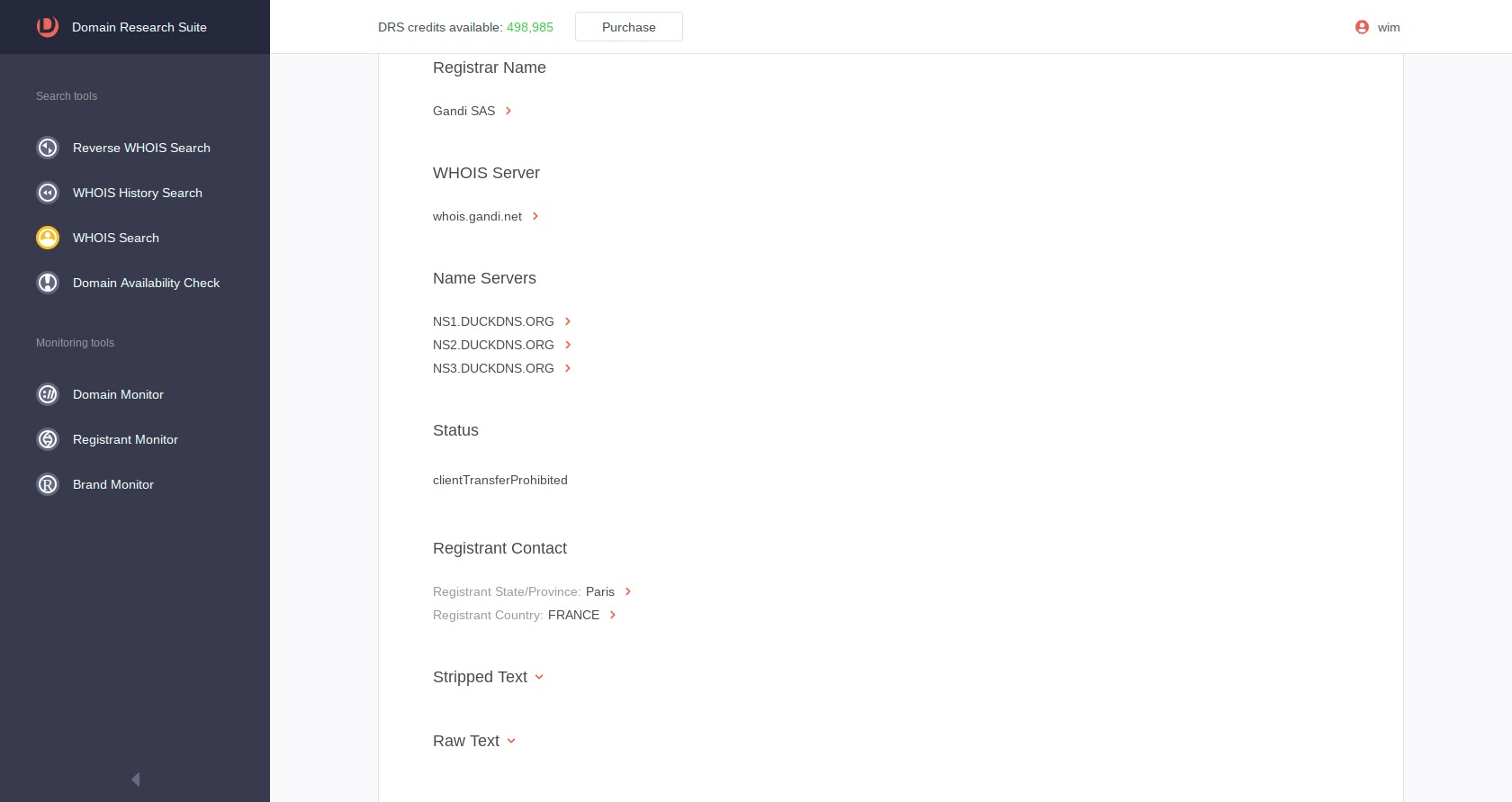
WHOIS record of https://x-finitycomcastboxappsuitnewteam.duckdns.org
When we run a WHOIS history of https://x-finitycomcastboxappsuitnewteam.duckdns.org in WHOISXMLAPI Domain Research Suite we find that the domain has no history of changes at all.
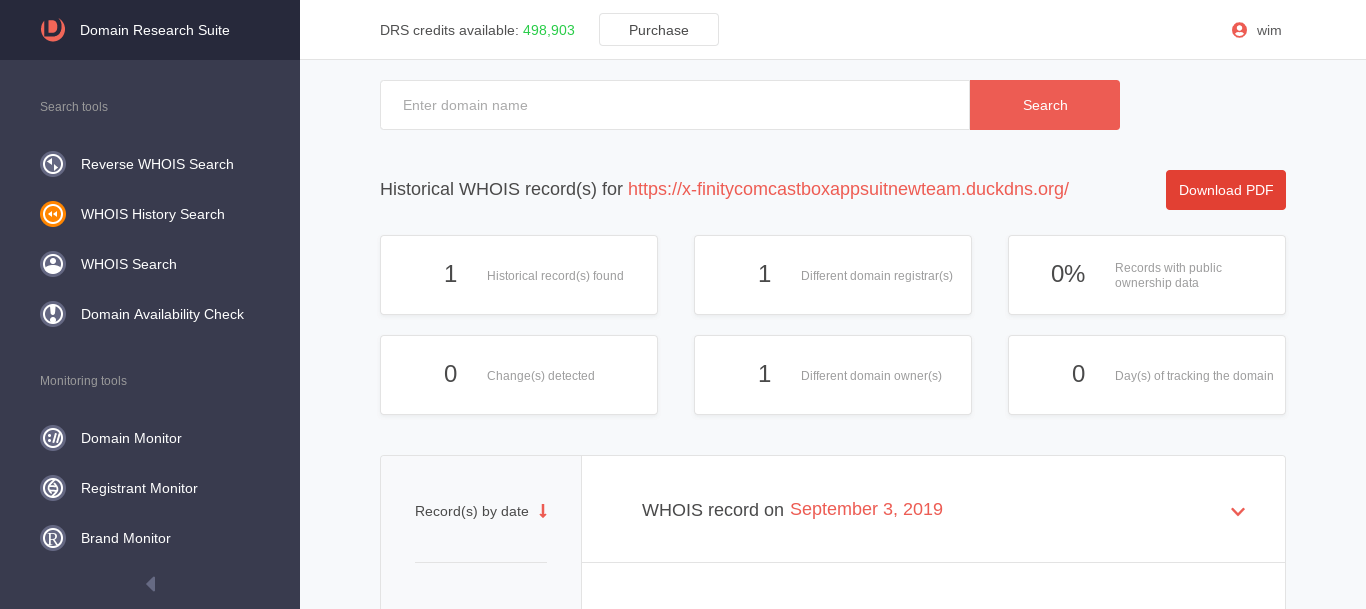
WHOIS HISTORY FOR https://x-finitycomcastboxappsuitnewteam.duckdns.org/
Instead, what we find is that the duckdns.org service masks the registration information of the originator of https://x-finitycomcastboxappsuitnewteam.duckdns.org/ .
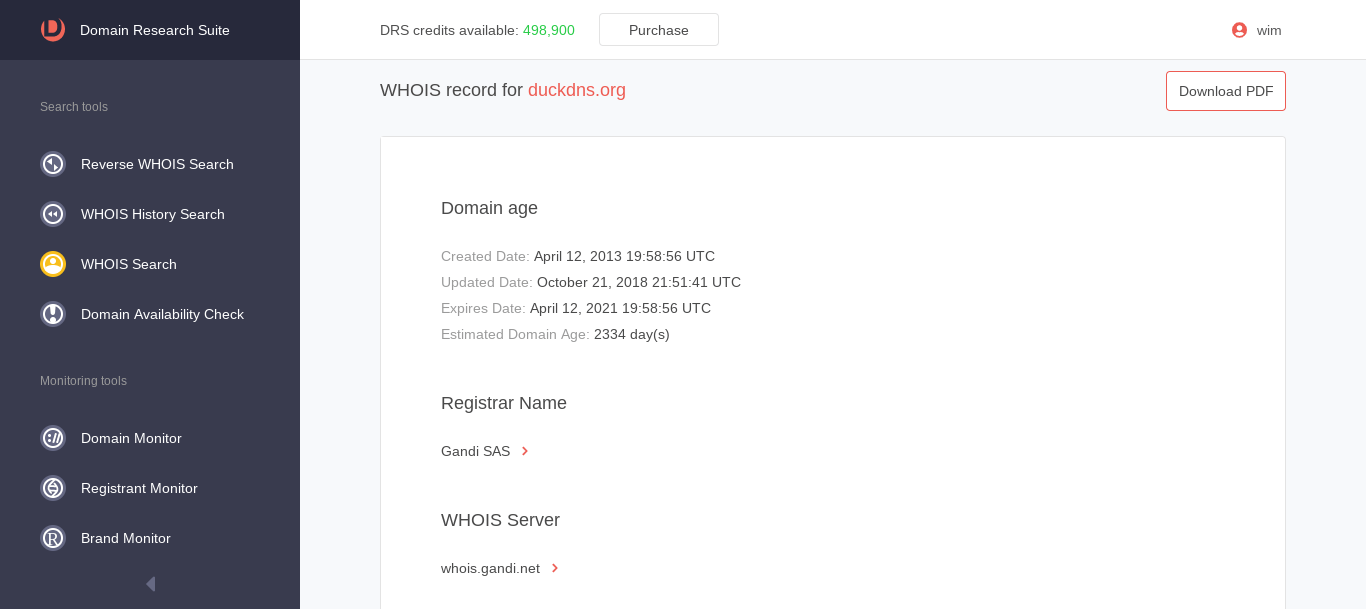
WHOIS HISTORY FOR duckdns.org
Indeed, in ThreatIntelligencePlatform.com Domain Name Analysis, the record for duckdns.org shows that the domain redirects calls to other domains. Those redirects mask the origins of domains that rely on the DDNS service.
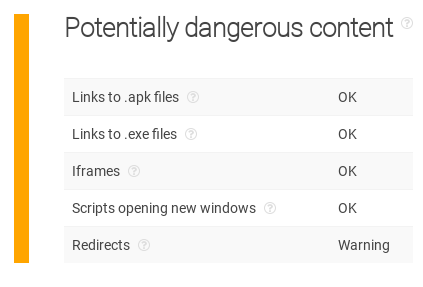
Warning for duckdns.org
When we run the ThreatIntelligencePlatform.com Domain Name Analysis on the domain name https://x-finitycomcastboxappsuitnewteam.duckdns.org/, everything looks legitimate except a record showing that it failed the Certificate Validity From date test.
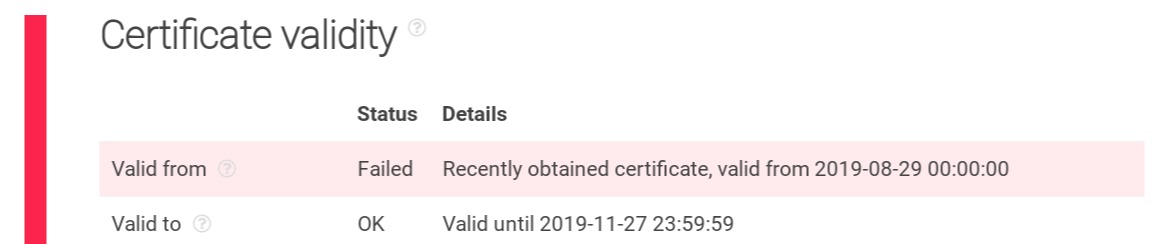
WHOIS record for https://x-finitycomcastboxappsuitnewteam.duckdns.org/
The fact that Certificate validity has failed makes one doubt that the registrant of the domain is also the owner of the domain. To recap, in the WHOIS Search the only identifying information was Paris, France (wherein Paris was a State).
A failed Certificate Validation can also arise because of the administrator’s use of a Dynamic DNS (DDNS) provider instead of a valid DNS service. Valid DNS services can grant domains the records they need to create certificates.
A Poke Around the Fake Website
So, while we’ve established the website is fake, what specific information is the portal seeking for users to divulge? By examining the links on the site, we can see where innocent users can find themselves in trouble. For instance, the Create user id and password page requests users to enter their phone number or the United States Social Security Number. While hackers can use the phone number to build up a profile of a hacking target, the Social Security Number gives criminals access to a wealth of access to commercial and governmental resources.
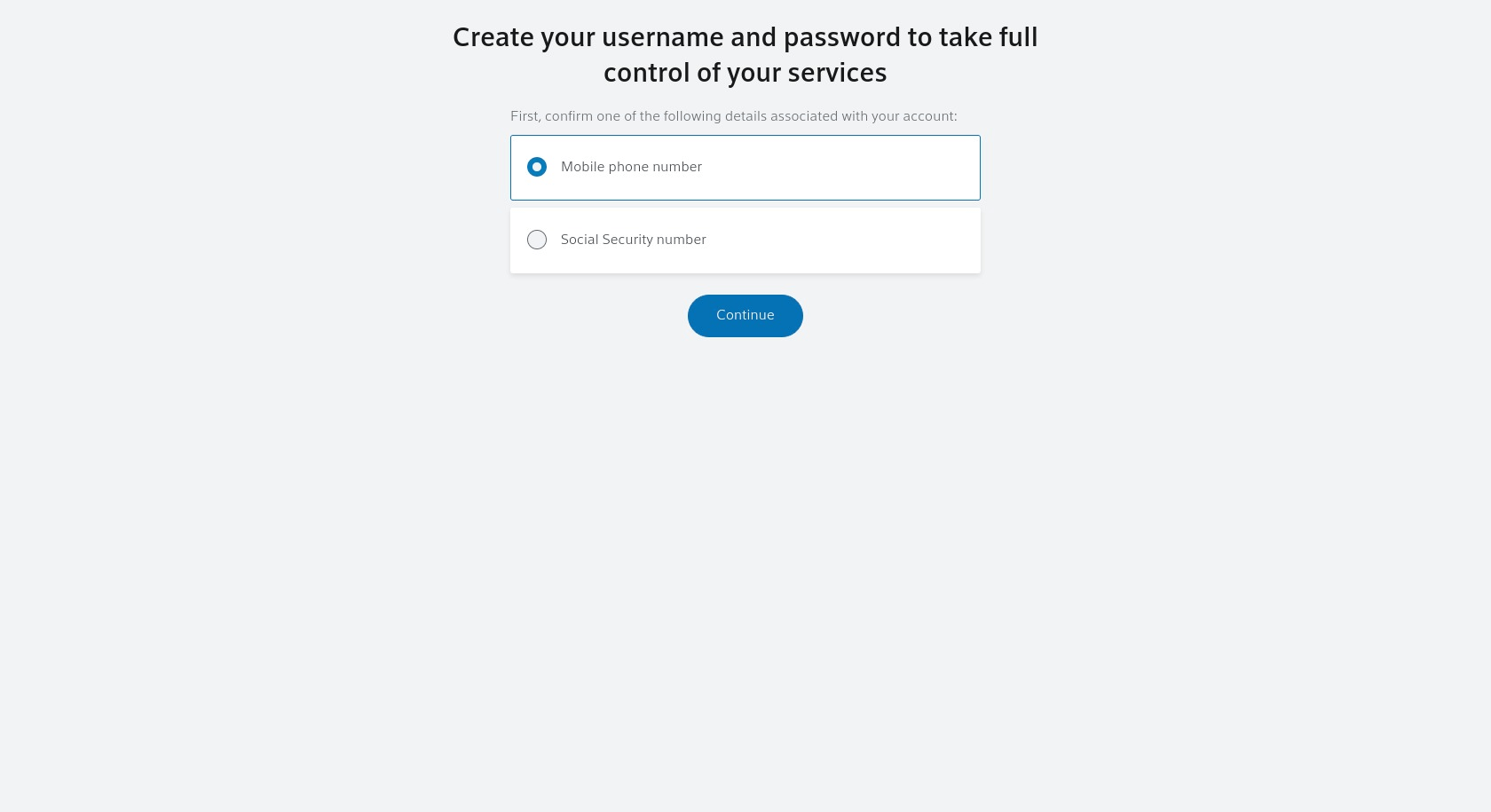
Individual services log-in screen
The address indicates that the login screen is also not associated with the authorized Comcast website: https://idm.xfinity.com/myaccount/create-uid?execution=e2s1
When we type in the root domain name idm.xfinity.com, the website displays a generic password reset screen: https://idm.xfinity.com/myaccount/account-selector?execution=e3s1
The “forgot your user name or password” links on the primary page lead users to the same screen, with a slightly different wording.
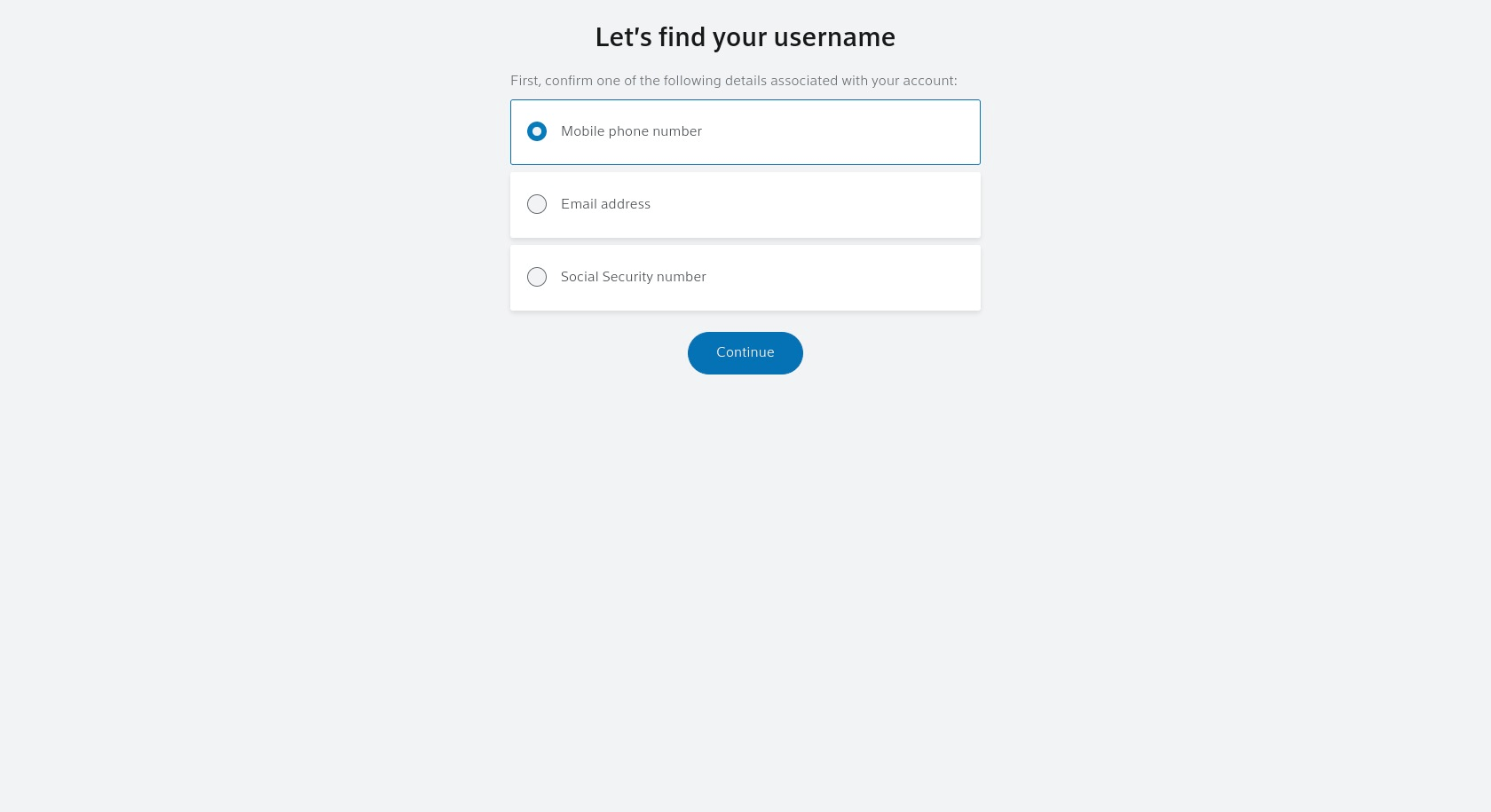
Forgot your username response (https://idm.xfinity.com/myaccount/lookup?execution=e2s1)
The screen asks the user for his/her email address, Xfinity user id, or telephone number. Any one of these pieces of information helps hackers target a range of the user’s accounts, not just their Xfinity login. As an uninformed user may recklessly type in their identification information into any of the contact details screens, the hackers will be able to go to the real Xfinity website with the information to take over the user’s account.
The idm.xfinity.com domain may be directly connected to the database that captures user information. Typing the address into a browser does not connect to any website. Our researchers assume the hackers have taken the site offline.
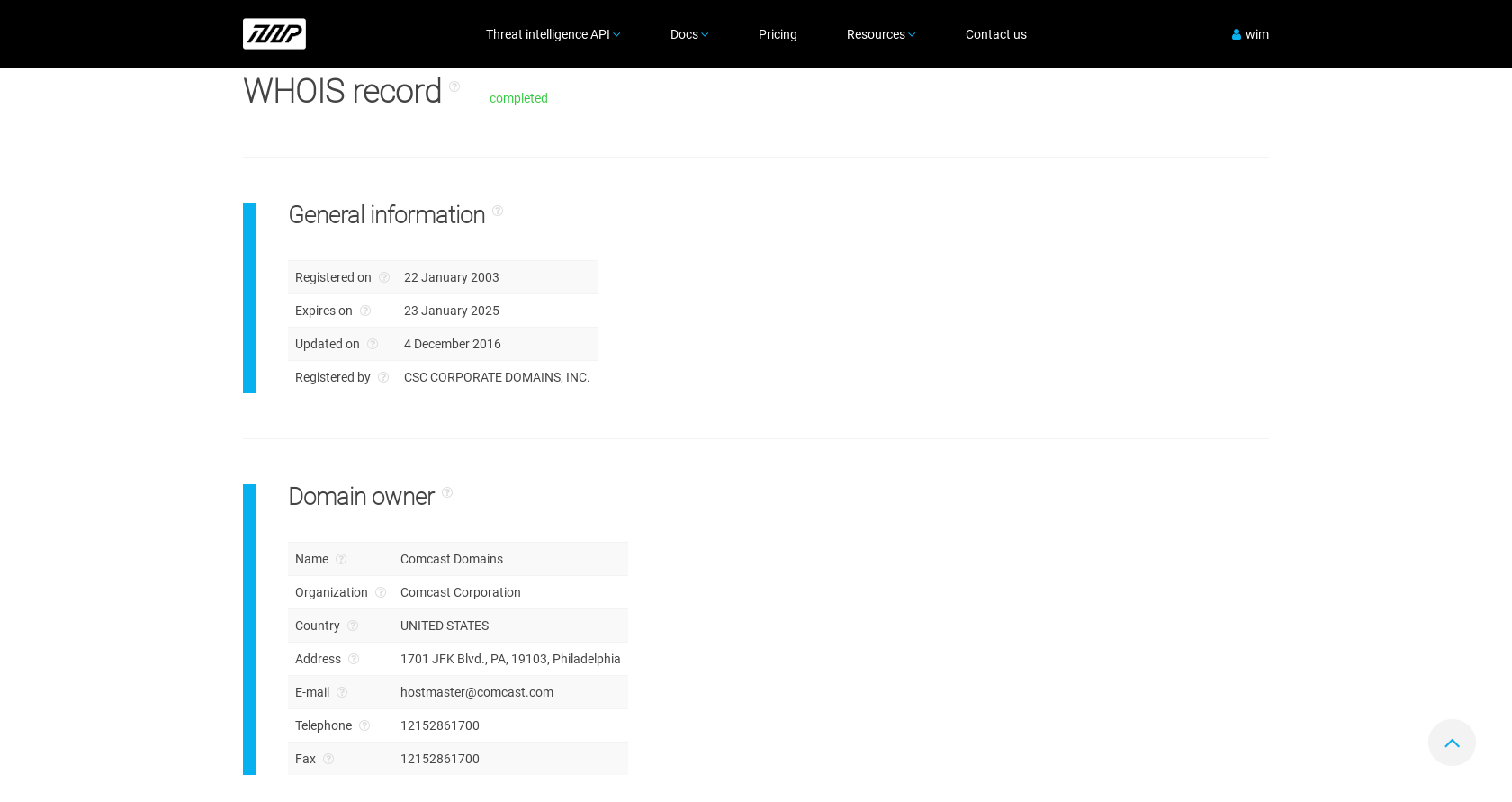
The WHOIS record for idm.xfinity.com
The WHOIS record for idm.xfinity.com does not display any untoward data.
Researchers ran a Reverse WHOIS search of the domain registration company CSC Corporate Domains in WHOISXMLAPI Domain Research Suite.
Reverse WHOIS of CSC Corporate Domains, Inc. (no idm.*)
We did not find any additional domains with the prefix idm.*, nor any that included the prefix xfinity*.
Reverse WHOIS of CSC Corporate Domains, Inc. (no xfinity.*)
However, the inconsistency becomes apparent when researchers compare the WHOIS record to the SSL certificate data for the domain.
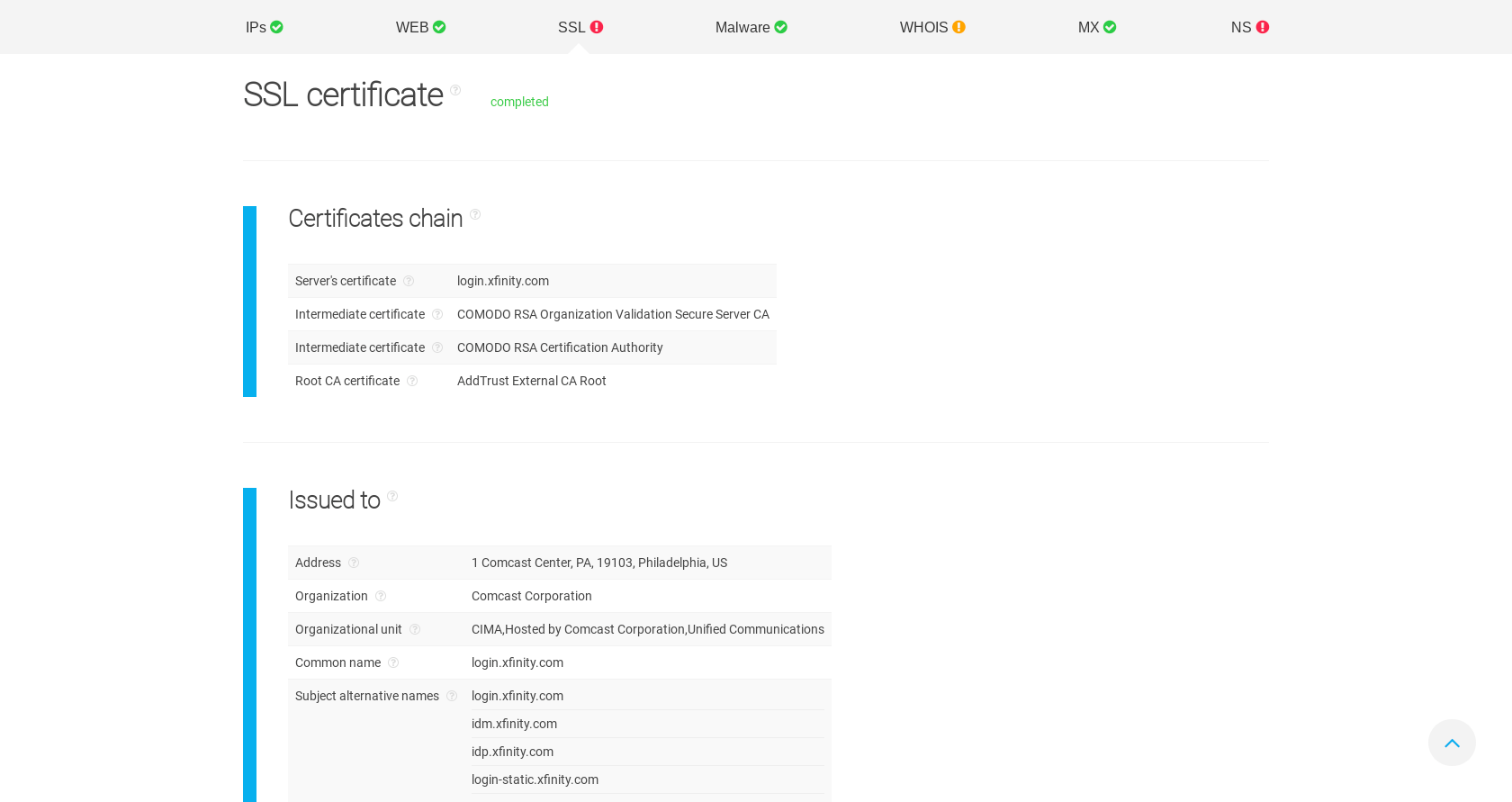
Certificates record for idm.xfinity.com displays organization and address information.
ThreatIntelligencePlatform.com Domain Name Analysis SSL Certificate record for idm.xfinity.com displays registration contact information inconsistent with current files. A quick google on the address displays a different address for Comcast Corporation. Further, the alternate addresses listed in the WHOIS record also do not display any websites.
Just like the Certificate validation for https://x-finitycomcastboxappsuitnewteam.duckdns.org/, idm.xfinity.com fails the test. The administrator apparently registered the certificate of idm.g.xfinity.com as idm.xfinity.com’s own.
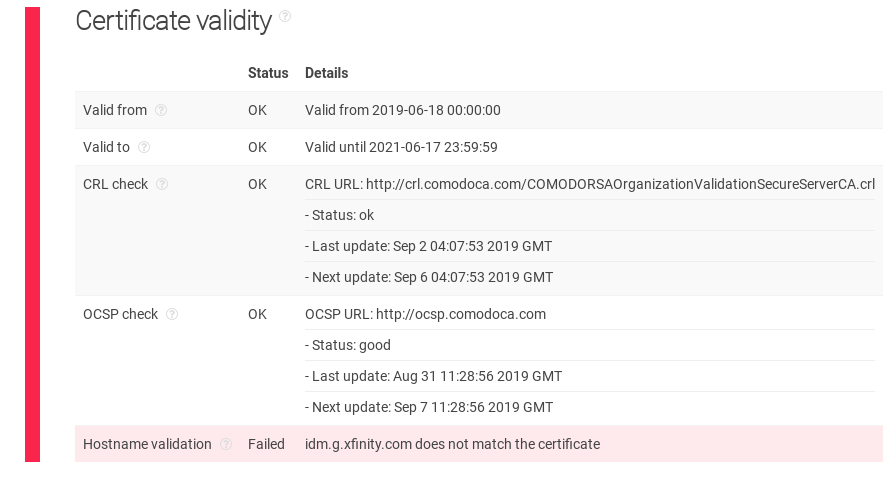
Idm.xfinity.com certificate validity fails
The WHOIS record shows additional, explicit warnings for Idm.xfinity.com, including:
- Found name servers don't provide A record for the domain
- The Configuration does not meet best practices: some name servers are located on a single ASN
- In the SOA record configuration check, the Serial number format has a warning that “Although the serial number is valid, it's not following the general convention: 6039,” and “The minimum TTL is 60. Recommended range is [3600 .. 86400]”
Nevertheless, website links to forms meant to capture user information consistently use the idm.xfinity.com domain, including ‘Reset your password’, ‘Let’s find your username’, and a link to a screen for a Quick Pay without Logging In.
Quick pay without logging in (https://idm.xfinity.com/myaccount/account-selector?execution=e3s1)
So, Who Is Behind the Phishing Site?
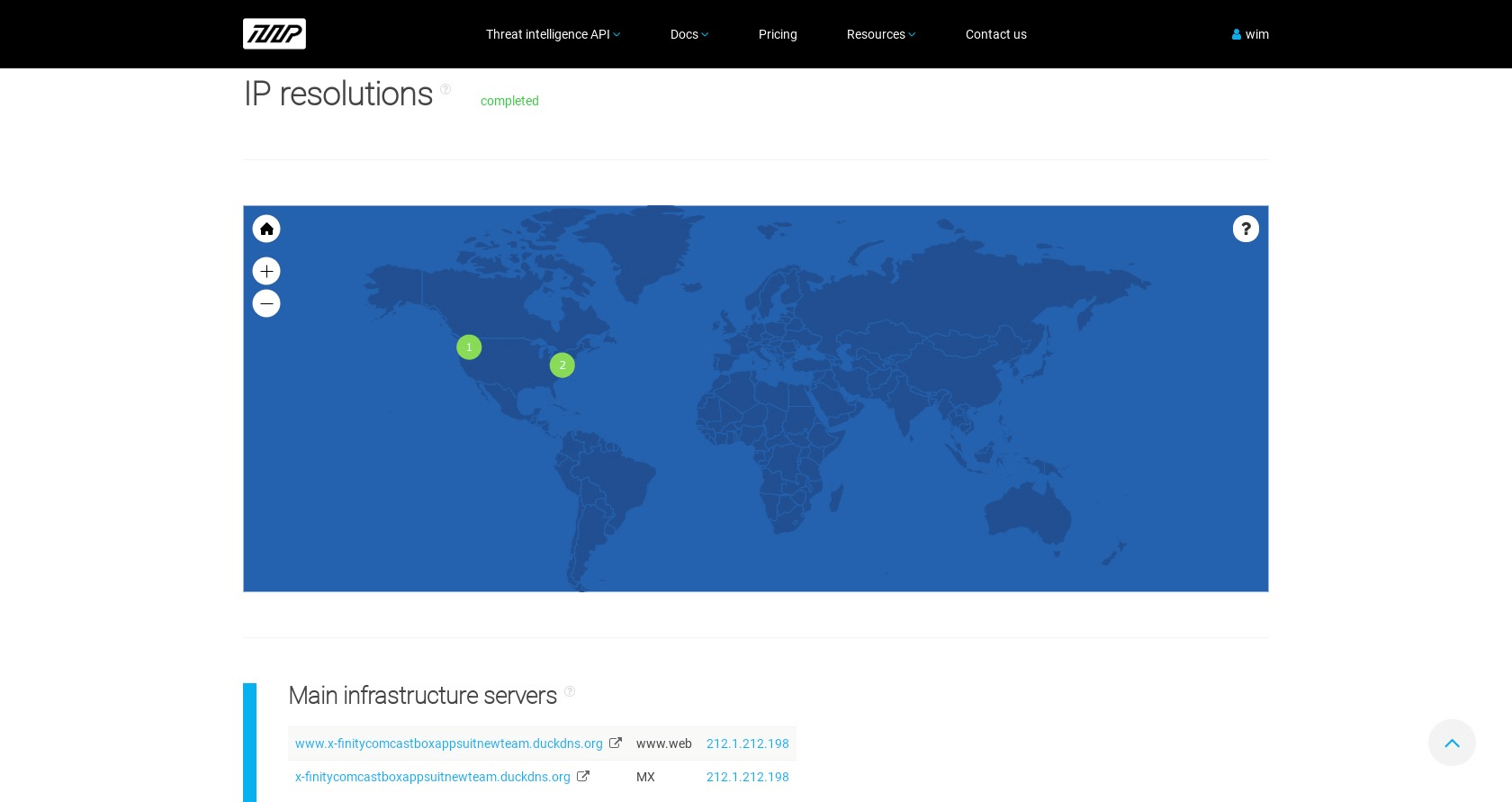
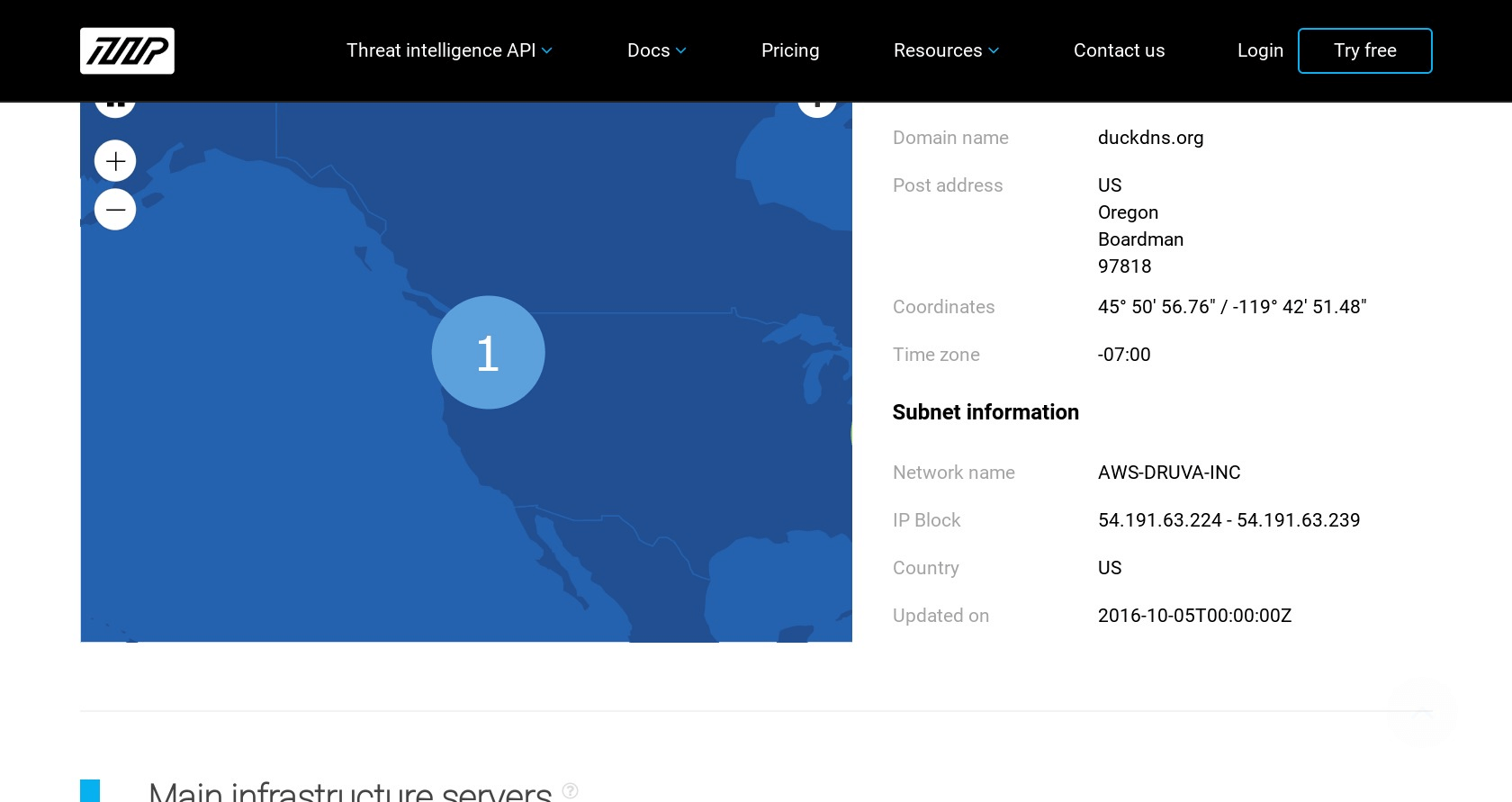
Through ThreatIntelligencePlatform.com’s Domain Name Analysis, we can resolve the domain name of the primary fake website at https://x-finitycomcastboxappsuitnewteam.duckdns.org/ to the IP address 54.191.209.253.
IP resolution of the fake website at https://x-finitycomcastboxappsuitnewteam.duckdns.org/
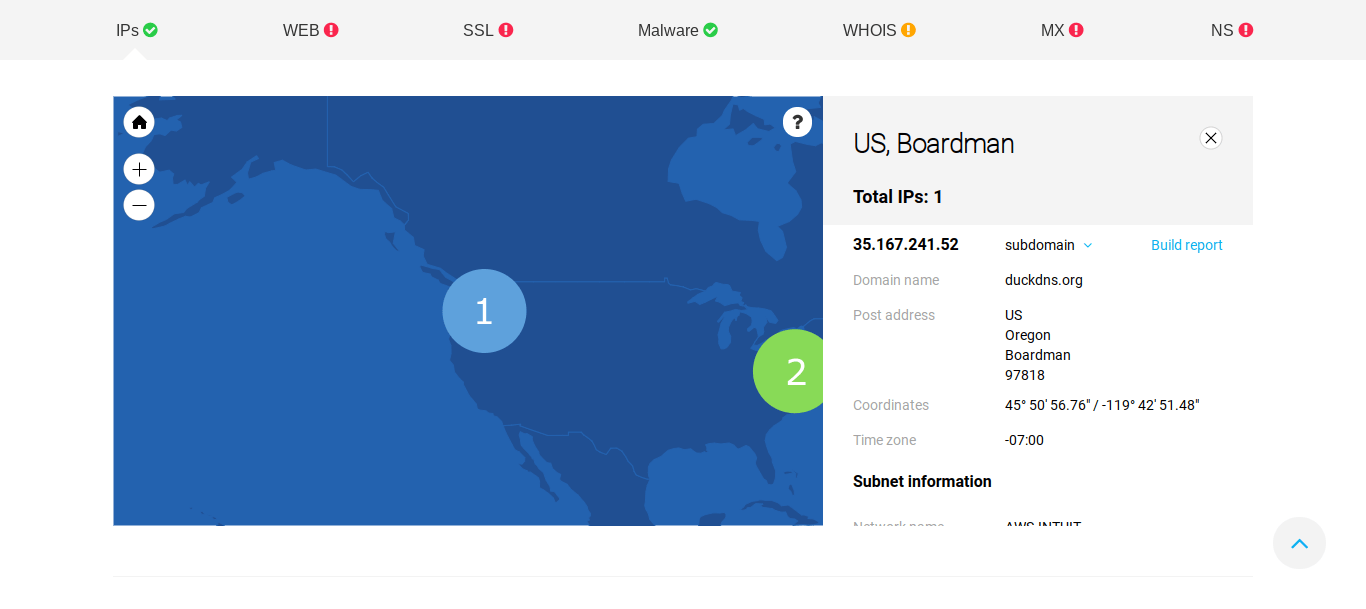
ThreatIntelligencePlatform.com’s Domain Name Analysis displays several geolocations for the resolution of DuckDNS.org IP designations. However, there is one IP address that stands out: 35.167.241.52.
IP resolution of the fake website at duckdns.org
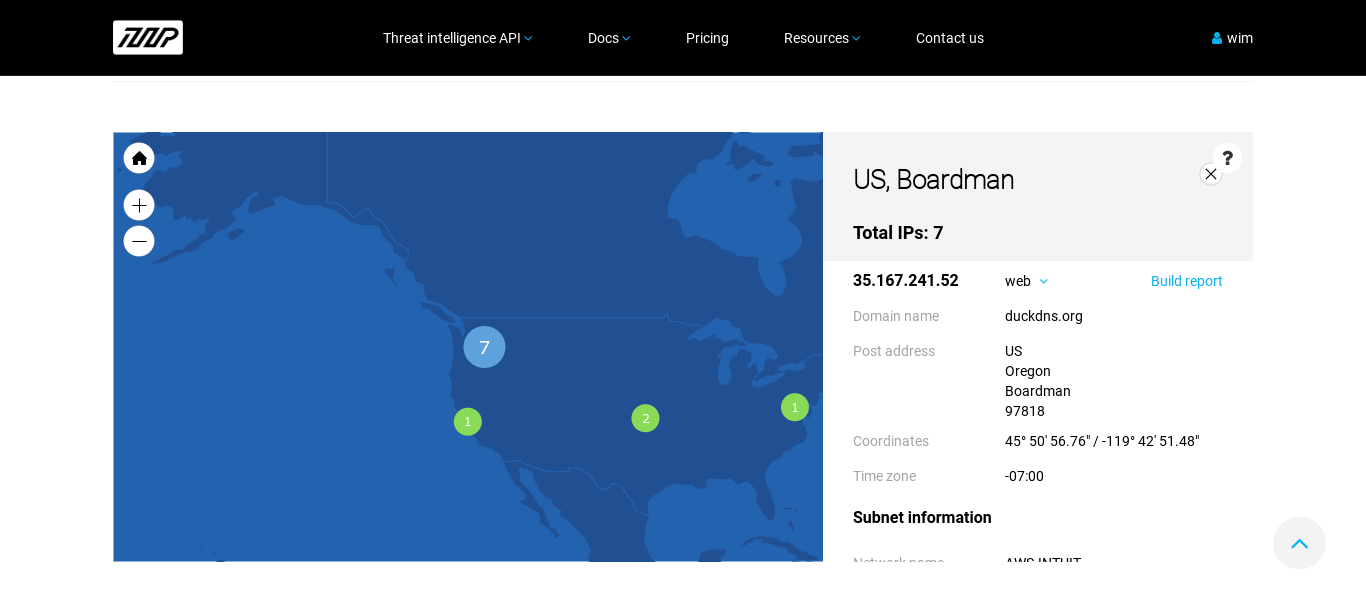
The geolocation for the IP address corresponds with the one for the website at https://x-finitycomcastboxappsuitnewteam.duckdns.org/. On the map that includes the United States and Europe, the locations for https://x-finitycomcastboxappsuitnewteam.duckdns.org/ and for duckdns.org converge in one location: Boardman, Oregon.
IP resolution of the fake website at https://x-finitycomcastboxappsuitnewteam.duckdns.org/
Boardman is the location of one of Amazon’s web service (AWS) centers. Resolving the geolocations of duckdns.org also reveals the locations of AWS data centers.
It seems that the author of the fraudulent Xfinity website is well hidden by the duckdns.org DDNS service, another “benefit” of Dynamic Domain Name Servers. The lack of clear ownership and registration of the site combined with the inconsistencies the researchers found in the DNS infrastructure records point to a cyber-effort meant to defraud and obfuscate.
Cybersecurity Isn’t Just for Techies Anymore
The data that the WHOISXMLAPI.com Dashboard Domain Research Suite and the ThreatIntelligencePlatform.com Domain Name Analysis enable researchers to assemble a picture and craft a narrative of criminal online behavior. In this instance, we explored the domain infrastructure of a phishing website design capture user credentials and perhaps even funds. Forensics specialists can also use the toolkits to supplement efforts to discover the parties infringing on brand equity and intellectual property. Fraud investigators can also use the tools to follow the trails of shell companies and laundering operations.
Further, the GUI interfaces of the toolkits and the displays of records lend themselves well to creating reports for infosec colleagues, business managers, and courts of law. Whenever professionals need to understand domain-level data, cybersecurity professionals and law enforcement investigators can use the toolkits to draft easy-to-read narratives for non-technical readers to digest effortlessly.
Meanwhile, every day, hackers create hundreds of new phishing websites intended to defraud and steal from people. WHOISXMLAPI.com and ThreatIntelligencePlatform.com offer just the right kind of tools to unmask criminals and get the right information across to those who need it most.


































